Operating Systems News
Ubuntu
12

Image Credit: Ubuntu
How is Livepatch safeguarded against bad actors?
- Canonical Livepatch is a security patching automation tool for the Linux kernel, aimed at providing reboot-less security updates while prioritizing security and operational convenience.
- To safeguard against bad actors, Livepatch introduces Secure Boot for trusted kernel running and module signature verification to ensure only trusted code is loaded into the kernel at runtime.
- Livepatch Client is distributed as a tamper-proof, self-updating snap application with strict confinement and granular system access. A certificate-based trust model ensures Livepatch updates are from a trusted source.
- Collaboration between Livepatch and kernel engineering teams, along with Launchpad's role in maintaining valid certificates, ensures the integrity and security of Livepatch updates to prevent misuse by bad actors.
Read Full Article
Like
Macrumors
365

Image Credit: Macrumors
Delta Emulator Developer Recreates Retro Game Boy Camera Experience on iPhone
- Riley Testut, the developer behind Delta Game Emulator and AltStore, is set to release a new app named Delta Camera.
- Delta Camera is designed to replicate the style of the Game Boy Camera, offering a retro photography experience on the iPhone.
- The app features a Game Boy Camera-like interface and captures images with a vintage aesthetic, while also providing modern functionalities such as Camera Control support and manual exposure.
- Testut's Delta Camera app, inspired by the 1998 Game Boy add-on, will be released later this year and is currently accessible to AltStore Patreon subscribers.
Read Full Article
21 Likes
Macdailynews
386

Image Credit: Macdailynews
Unreleased Apple audio product spotted in code
- An unreleased Apple audio product, potentially AirPods Pro 3, was found in the codebase with the identifier 8239.
- Rumors suggest the AirPods Pro 3 might launch in 2025 or face a delay to 2026, featuring design updates, a new H3 chip, health monitoring features, enhanced audio, and other improvements.
- Speculated features for AirPods Pro 3 include a redesign, new chip for improved audio processing, health monitoring capabilities, better ANC, and advanced features like live translation and enhanced Find My functionality.
- While uncertainties exist regarding specific features and release dates, the potential pricing for AirPods Pro 3 is expected to remain around $249, with conflicting reports about the launch year and feature updates.
Read Full Article
23 Likes
Macstories
4

Image Credit: Macstories
Apple Opens Up New App Distribution Options in the EU, Along with New and Updated Fees
- Apple is making changes to its App Store rules in the EU to comply with the European Commission's order and avoid fines.
- Developers can now promote in-app offers for digital goods and services that can redirect users outside the app.
- New fees for developers offering external purchases include acquisition fees, store services fees, and a Core Technology Commission.
- Developers in the EU can sell their apps not only through alternative app marketplaces but also on their own websites, subject to specific requirements.
Read Full Article
Like
Discover more
- Programming News
- Software News
- Web Design
- Devops News
- Open Source News
- Databases
- Cloud News
- Product Management News
- Agile Methodology News
- Computer Engineering
- Startup News
- Cryptocurrency News
- Technology News
- Blockchain News
- Data Science News
- AR News
- Apple News
- Cyber Security News
- Leadership News
- Gaming News
- Automobiles News
Macdailynews
199

Image Credit: Macdailynews
Apple updates App Store rules and fees on outside links in EU to comply with antitrust order
- Apple updated its App Store rules and fees in the EU to comply with antitrust orders, allowing developers to direct customers outside the store for payment.
- Developers will incur a 20% processing fee for App Store purchases, with reduced fees for those in Apple’s small-business program.
- Developers sending customers outside the App Store for payment will face a minimum fee of 5% and a maximum of 15%, along with the ability to use multiple links for external payment.
- Apple made the changes to avoid a potential 500 million euro fine from EU antitrust regulators and plans to appeal the decision.
Read Full Article
12 Likes
TechCrunch
38

Image Credit: TechCrunch
Windows killed the Blue Screen of Death
- The iconic Blue Screen of Death (BSOD) in Windows is getting a makeover after nearly 40 years, changing to the Black Screen of Death (BSOD).
- This change is part of Windows updates following the CrowdStrike outage last year that affected 8.5 million Windows devices, leading to the Windows Resiliency Initiative for enhanced security features and less disruptive restarts.
- The new Black Screen of Death is introduced as a 'simplified UI,' with Microsoft not directly acknowledging the transition and aiming for a smoother user experience.
- The BSOD has been a familiar indicator of system errors since its debut in Windows 1.0 in 1985, with the recent change sparked speculation on reasons behind the shift from blue to black.
Read Full Article
2 Likes
Siliconangle
389

Image Credit: Siliconangle
Research shows open source fuels economic growth, AI innovation
- New research from The Linux Foundation shows that open source contributes $9 trillion in global value, factoring in time saved from not developing software covered by open source and profits from companies using open source in production.
- The estimation process for the value of open source is evolving with the inclusion of AI, leading to a need for more data on data itself, models, usage, and how companies leverage it.
- Calculating the value of open-source AI is complex due to significant upfront investment in training, which changes the scope of people's jobs and enhances productivity.
- Contributing to open source projects can significantly increase economic value for both the contributor and future users, potentially doubling productivity compared to those who only use open source without contributing back.
Read Full Article
23 Likes
Macdailynews
140

Apple’s ‘F1,’ starring Brad Pitt, expected to top box office, but projections are all over the map
- Apple's 'F1' movie with Brad Pitt aims for $50-$60 million debut.
- Projections vary with some predicting $35-$40 million for the race drama.
- The film is a major move for Apple into the theatrical space internationally.
- 'F1' eyes $75 million from 77 markets, distributed by Warner Bros.
Read Full Article
8 Likes
Silicon
339

Image Credit: Silicon
Microsoft Offers Update Lifeline For Windows 10 Users
- Microsoft is offering a temporary lifeline for Windows 10 users who cannot or will not upgrade to Windows 11 due to hardware requirements like TPM 2.0 and UEFI with Secure Boot.
- Windows 10 updates are set to end on 14 October 2025, but many users are locked out of upgrading to Windows 11.
- Microsoft encourages Windows 10 users to switch to Windows 11, but those with incompatible machines may need to replace them.
- For individual consumers, Microsoft is providing an enrollment wizard with options like using Windows Backup, redeeming Microsoft Rewards points, or paying a one-time fee of $30 to extend support until 2026 for personal computers.
Read Full Article
20 Likes
Hackaday
72

Image Credit: Hackaday
Rust Drives a Linux USB Device
- Using libusb in Rust, a user-space USB device driver was created for a USB hub with lights and gadgets.
- The main challenge was understanding the protocol and USB stack, including configurations, interfaces, and endpoints.
- Ancillary topics like setting up udev are also covered in the documentation.
- The Rust program, aided by libusb, efficiently handles threads, interrupts, and typical device driver tasks in user space.
Read Full Article
4 Likes
Macdailynews
288

Image Credit: Macdailynews
Trump Mobile quietly drops ‘Made in America’ claim for ‘T1 Phone’
- Trump Mobile, a venture licensed by The Trump Organization, has removed 'Made in America' claim from its $499 T1 smartphone.
- Initially marketed as 'Made in America,' the T1 Phone now uses vaguer language like 'Proudly American' and 'designed with American values.'
- Speculation arose that the T1 Phone is a rebranded Chinese device, leading to skepticism about the feasibility of its original claim.
- The T1 Phone's website changes include altering specifications and launch dates, sparking discussions about the challenges of producing smartphones in the U.S.
Read Full Article
17 Likes
Dev
72

Image Credit: Dev
Intel GPU Slowdowns From Mitigations Could Be Reversed—Ubuntu Is Testing It
- Canonical is considering disabling Intel GPU security mitigations to potentially boost performance by up to 20% on Ubuntu.
- Intel GPUs are affected by speculative execution vulnerabilities, leading to performance slowdowns of up to 20% in compute-heavy tasks.
- Canonical is evaluating the trade-off between performance gains and security risks, noting that no known GPU attacks exploiting these vulnerabilities have occurred yet.
- The decision to disable GPU mitigations on Ubuntu could influence how other Linux distributions and possibly Windows handle Intel GPU security in the future.
Read Full Article
4 Likes
Rockpapershotgun
399

Image Credit: Rockpapershotgun
Surprise! Nuclear Throne has a new update that's mostly for people that insist on only playing games that can do 60fps
- Nuclear Throne, an indie game nearing its 10th anniversary, has received a new beta build update mainly focused on offering 60fps and 120fps support as well as new aspect ratios and a controls menu.
- The update, available now for players who opt into the beta build on Steam, also includes a new Melting loading screen tip and quality of life improvements.
- Developer Vlambeer intends to integrate these enhancements into the main game in the future, along with additional features not specified in the beta update.
- To access the update, players can follow a simple process within the Steam library settings to switch to the 'openbeta_win64' branch.
Read Full Article
24 Likes
Idownloadblog
407
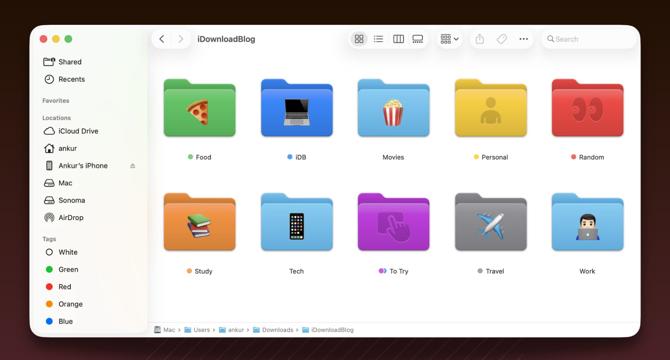
Image Credit: Idownloadblog
How to personalize folder icons on your Mac with custom color, emoji, and symbols
- macOS Tahoe 26 allows users to personalize folder icons on Mac with color, emoji, and symbols.
- Users can add symbols or emojis to folder icons by customizing the folder and selecting from a wide range of options.
- Changing the color of folder icons is now easier with macOS Tahoe 26 by applying tags to folders.
- Customized folder icons on iCloud Drive are visible on Mac and iOS devices, but not on Windows or the web.
Read Full Article
24 Likes
Dev
59

Image Credit: Dev
Mastering Linux File Editors: From First Keystroke to Confident Command-Line Editing
- Encounter the intrigue of Linux file editors, navigating from novice to proficient user.
- Learn about essential editors like vi, vim, ed, ex, emacs, and pico and their significance.
- Improve speed and efficiency by mastering terminal editors for versatile command-line editing.
- Discover essential commands, modes, and scenarios where expertise in these tools is invaluable.
- Enhance productivity, self-reliance, and problem-solving skills through Linux file editor proficiency.
Read Full Article
3 Likes
For uninterrupted reading, download the app